What Best Describes Ips Comparing to Ids
The IPS security system does prevent any packages from being delivered into the system network. That is because IPS stands between the external world the internet and your local area network.
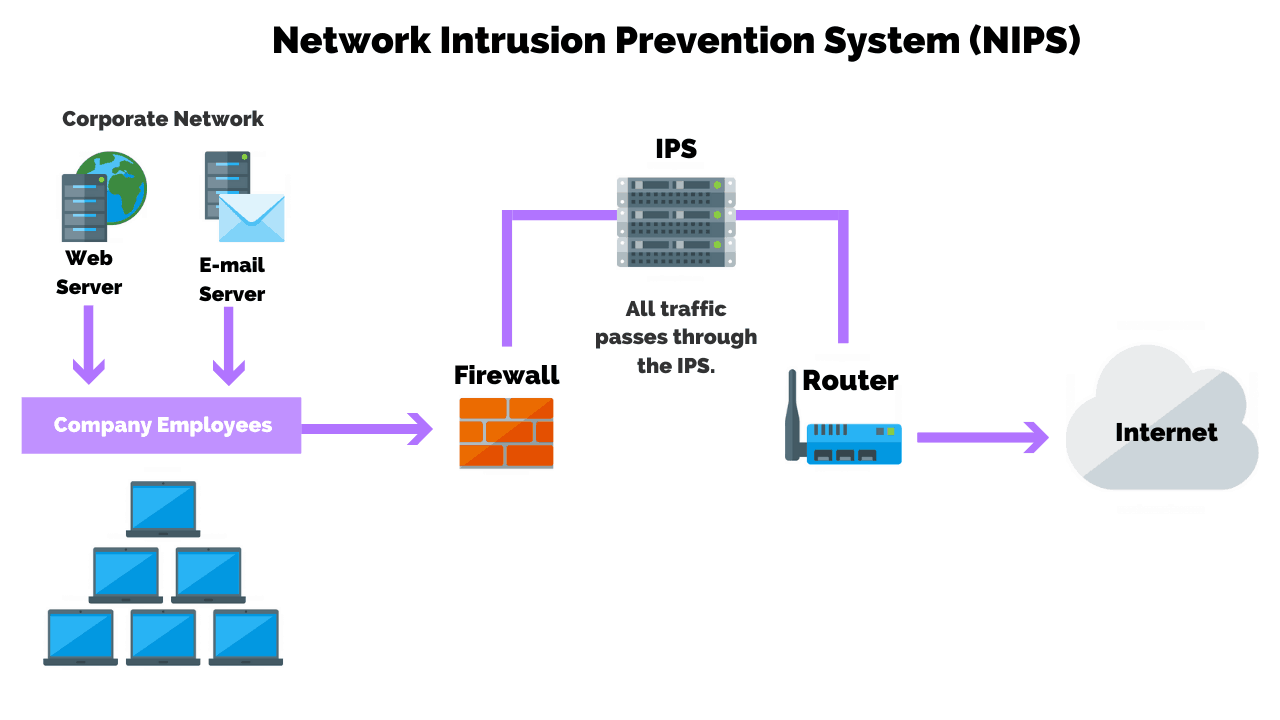
Intrusion Detection Vs Prevention Systems What S The Difference
They both prevent malicious traffic from infiltrating the network B.
. Question 1 666 666 pts Which best describes IPS compared to IDS. It relies on the source the destination addresses and the ports. While Firewall blocks and filters network traffic IDSIPS looks to identify malicious activity and alert an administrator to prevent cyberattacks.
IPS usually uses a combination of traffic and file signatures and heuristic analysis of flows. Both systems compare network traffic and packets against a database of cyber threats. The IDS contains a database of known attack signatures and compares the inbound traffic against to the database.
The main difference being that firewall performs actions such as blocking and filtering of traffic while an IPSIDS detects and alert a system administrator or prevent the attack as per configuration. Intrusion Detection Systems IDS. With signature-based detection the platform scans for patterns that indicate vulnerabilities or exploitation attempts.
Main deference between the two is unlike IDS IPS actively takes steps to prevent or block intrusions that are detected. The main difference between the two security systems is that one monitors while the other controls. The major difference between Intrusion Prevention Systems IPS and Intrusion Detection Systems IDS is that IPS devices operate inline with the traffic meaning they are placed in the middle of the traffic flow and all packets pass through the inspection device while IDS devices only receive a copy of the traffic so they can analyze it.
The systems then flag offending packets. Which of the following best describes how an IPS is similar to an IDS. Use an int primary key and let the database generate the primary key when you insert a row.
An IDS Intrusion Detection System is the predecessor of IPS and is passive in nature. IDS system security doesnt make any changes to the packets but scan them and check them thoroughly through a database for any threats. IPS is an abbreviation for Intrusion Prevention System a system which inspects traffic flowing through the network and blocks or else remediates flows with malicious traffic.
An IPS uses anomaly detection and signature-based detection similar to an IDS. Similar to a firewall IPS is deployed inline to the traffic flow. They both sit in the path of network traffic D.
The IPS sits behind the firewall and uses anomaly detection or signature-based detection to identify network threats. IPS is the shortened form of Intrusion Prevention Systems. IDS and IPS systems are two parts of network infrastructure that detect and prevent intrusions by hackers.
Can detect encrypted intrusions Because host-based IPS exists on the host where the data has been decrypted Can detect malicious activity that does not. IPS vs IDS both are the database containing known cyber Attack Signatures that compares network packets to cyber threats with a matching flag. This is pretty similar to a firewall when it is applied to a network.
How Intrusion Detection Systems IDS and Intrusion Prevention Systems IPS Work. Some experts consider intrusion prevention systems to be a subset of intrusion detection. An IDS is a system that monitors the network and detects inappropriate incorrect or anomalous activities while an IPS is a system that detects intrusion or an attack and takes active steps to prevent them.
While the lines between IDSIPS have become blurred over time some unique differences essential to note include. But security systems can go one step further and act to stop ongoing and future attacks. When an IPS detects an attack it can reject data packets give commands to a firewall and even sever a connection.
To give a bit of context and to explore why you might want to use NewId Ill discuss the pros and cons of each of the above approaches to generating primary keys. HIPS Host-based IPS vs NIPS Network-based IPS HIPS. They both use signatures to detect malicious traffic C.
Indeed all intrusion prevention begins with intrusion detection. The biggest difference between Firewall and IPSIDS is their basic function. An IPS on the other hand takes action itself to block the attempted intrusion or otherwise remediate the incident.
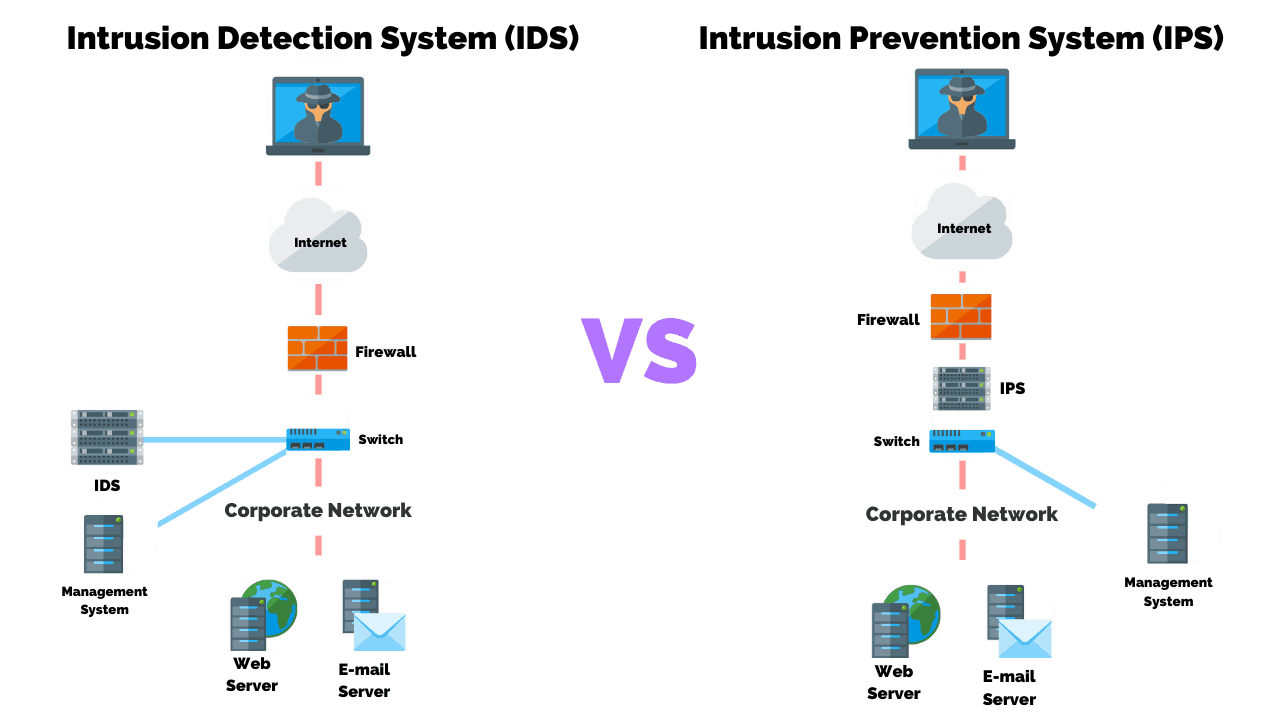
As shown from the network above Firewall with IDS this device is not inserted in-line with the traffic but rather it is in parallel placed out-of-band. A firewall allows traffic based on a set of rules configured. Intrusion Detection System IDS and Intrusion Prevention System IPS both are components of the network infrastructure.
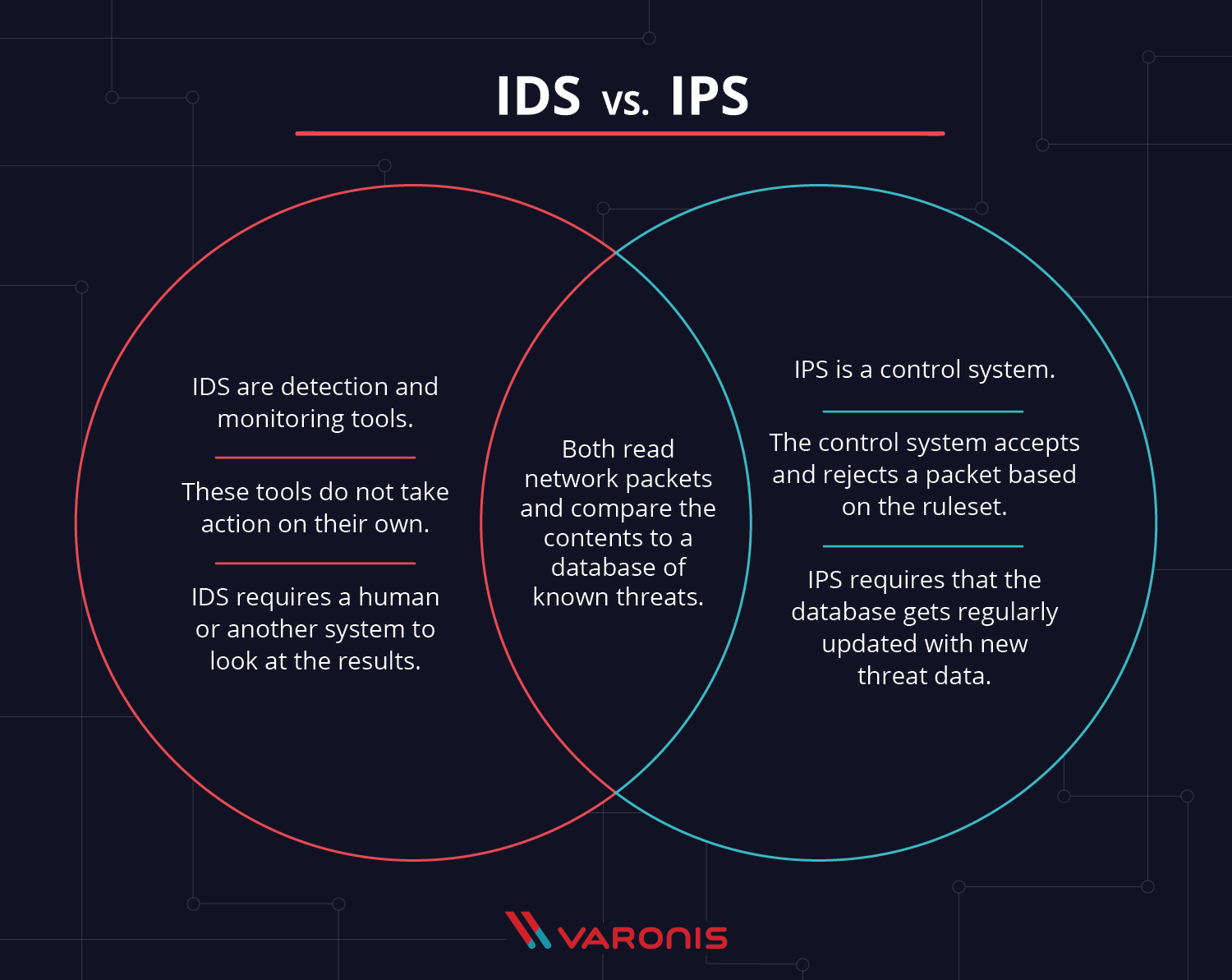
The primary difference between the two is that one monitors while the other controls. Intrusion Detection Systems IDS and Intrusion Prevention Systems IPS are both parts of the network infrastructure. Neither sits in the path of network traffic.
The main difference between them is that IDS is a monitoring system while IPS is a control system. The main difference is that IDS is a system for tracking while IPS is a system for regulation. In contrast IDS is a passive component typically not deployed inline and instead monitors the traffic flow via span or tap technology to.
IPS is designed to deny network traffic proactively. Use a Guid primary key generate the ID in your application and insert it with the row. An agent is placed on a system that sends back signs of suspicious activity to a central management console or writes to system logs.
IPS is an active network component that examines every passing packet and takes the correct remedial action per its configuration and policy. IDSIPS compare network packets to a cyberthreat database containing known signatures of cyberattacks and flag any matching packets. An IDS is designed to only provide an alert about a potential incident which enables a security operations center SOC analyst to investigate the event and determine whether it requires further action.
A passive device that detects and alertsd administrators An inline monitoring system that can modify the environment to block an attack An active device that detects and alertsd administrators A system used to analyze vulnerabilities aganist a host machine. The main difference between intrusion detection systems IDS and intrusion prevention systems IPS is that IDS are monitoring systems and IPS are control systems. Traffic passing through the switch is also sent at the same time to the IDS for inspection.
IDS wont alter network traffic while IPS prevents packets from delivering based on the contents of the packet similar to how a firewall prevents traffic by IP address.

Ids Vs Ips What Is The Difference
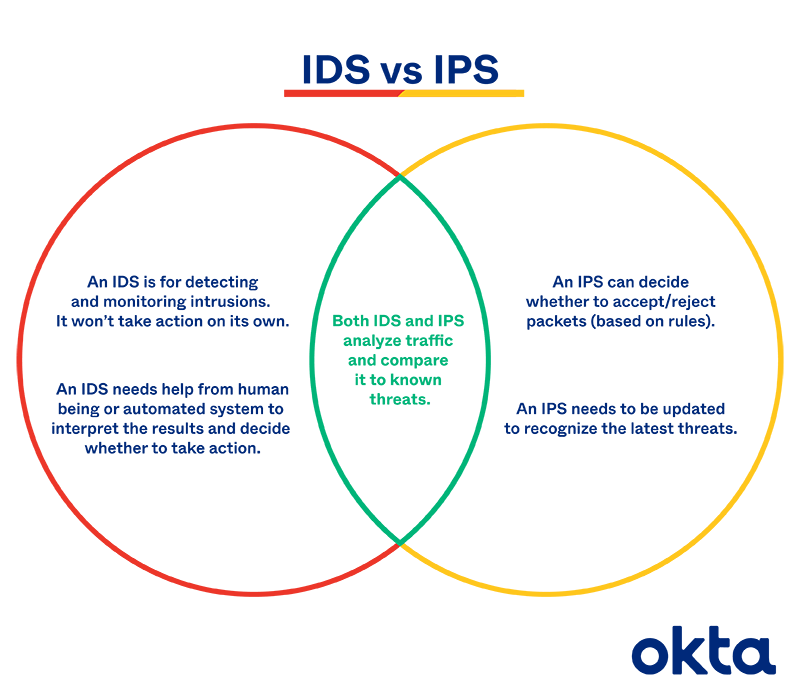
Ids Vs Ips Definitions Comparisons Why You Need Both Okta
Intrusion Detection Vs Prevention Systems What S The Difference

Ids Vs Ips A Comprehensive Guide To Network Security Solutions
0 Response to "What Best Describes Ips Comparing to Ids"
Post a Comment